Browserling has a new friend - Chrome 17, the new version of Google Chrome. It was released just today and we installed it on our browser platform already. This version is a lot about speed and especially regarding security.

Try it yourself right away from our browser-testing widget:
What's new in Chrome 17?
The most notable features are as follows:
- Updated Omnibox prerendering of pages.
- Download scanning protection.
- New extensions APIs.
- Improved History tab.
- Removal of "+" symbol from the "new tab" button.
- Limited support for changing user agent strings.
- Adjustable margins in print preview.
- Search engine synchronization.
- Disabled GAIA profile info.
Security
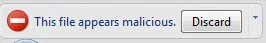
Google now will automatically check for you executable files like .exe and .msi whether they match with a built-in white list of programs considered safe. Then it will also check the source site, whether it is known for malicious downloads. If the file is from an unknown source, Chrome sends info of the site and the file to Google server where it performs a number of tests and machine learning analysis, accounting reputation and trustworthiness of files previously seen from the same publisher and Web site to estimate a result that is ultimately sent back to you, warning you if you are at risk. You can of course, turn this feature off.
Omnibox prerendering
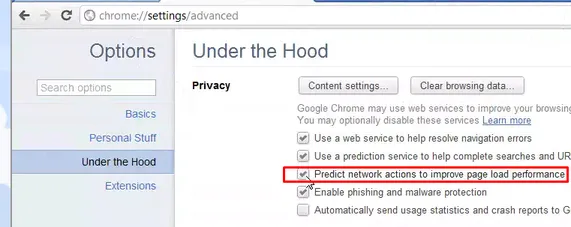
For those still not familiar with this concept, the omnibox preloading is when you begin typing in the addressbar (Google's omnibox) you start receiving a variety of suggestions that usually complete your typing. In Chrome 17 however, this feature will do more. It will also start pre-loading those websites so that if it guesses them right, the page will be loaded faster. That feature you can disable too from the options menu > Under the Hood.
Bug fixes in Chrome 17
- CVE-2011-3953: Avoid clipboard monitoring after paste event.
- CVE-2011-3954: Crash with excessive database usage.
- CVE-2011-3955: Crash aborting an IndexDB transaction.
- CVE-2011-3956: Incorrect handling of sandboxed origins inside extensions.
- CVE-2011-3957: Use-after-free in PDF garbage collection.
- CVE-2011-3958: Bad casts with column spans.
- CVE-2011-3959: Buffer overflow in locale handling.
- CVE-2011-3960: Out-of-bounds read in audio decoding.
- CVE-2011-3961: Race condition after crash of utility process.
- CVE-2011-3962: Out-of-bounds read in path clipping.
- CVE-2011-3963: Out-of-bounds read in PDF fax image handling.
- CVE-2011-3964: URL bar confusion after drag + drop.
- CVE-2011-3965: Crash in signature check.
- CVE-2011-3966: Use-after-free in stylesheet error handling.
- CVE-2011-3967: Crash with unusual certificate.
- CVE-2011-3968: Use-after-free in CSS handling.
- CVE-2011-3969: Use-after-free in SVG layout.
- CVE-2011-3970: Out-of-bounds read in libxslt.
- CVE-2011-3971: Use-after-free with mousemove events.
- CVE-2011-3972: Out-of-bounds read in shader translator.
Have fun cross-browser testing in Chrome 17!
Email this blog post to your friends or yourself!
Try Browserling!
Enter a URL to test, choose platform, browser and version, and you'll get a live interactive browser in 5 seconds!

 Subscribe to updates!
Subscribe to updates!
 BizSpark
BizSpark