Posted by on January 1, 2013
Chrome 24 was released today. We just added this new browser version to our cross-browser testing cloud. You can start testing your apps in this browser.
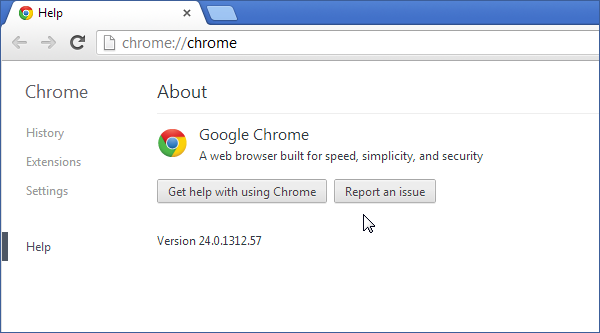
Try Chrome 24 in Browserling now!
New in Chrome 24
- Support for MathML.
- The HTML5 datalist element now supports suggesting a date and time.
- Experimental support for CSS custom filters.
- Update to Flash version 11.5.31.137.
- Improvements in speed and stability.
Developer News in Chrome 24
- Added performance.now() - Enables reliable, high-resolution timing of client-side performance.
- Added graphics requestAnimationFrame() - Offload animation repainting to browser for optimized performance. You should call this method whenever you're ready to update your animation onscreen. This will request that your animation function be called before the browser performs the next repaint.
Security Fixes in Chrome 24
- CVE-2012-5145: Use-after-free in SVG layout. Credit to Atte Kettunen of OUSPG.
- CVE-2012-5146: Same origin policy bypass with malformed URL. Credit to Erling A Ellingsen and Subodh Iyengar, both of Facebook.
- CVE-2012-5147: Use-after-free in DOM handling. Credit to Jose A. Vazquez.
- CVE-2012-5148: Missing filename sanitization in hyphenation support. Credit to Google Chrome Security Team (Justin Schuh).
- CVE-2012-5149: Integer overflow in audio IPC handling. Credit to Google Chrome Security Team (Chris Evans).
- CVE-2012-5150: Use-after-free when seeking video. Credit to Google Chrome Security Team (Inferno).
- CVE-2012-5151: Integer overflow in PDF JavaScript. Credit to Mateusz Jurczyk, with contribution from Gynvael Coldwind, both of Google Security Team.
- CVE-2012-5152: Out-of-bounds read when seeking video. Credit to Google Chrome Security Team (Inferno).
- CVE-2012-5153: Out-of-bounds stack access in v8. Credit to Andreas Rossberg of the Chromium development community.
- CVE-2012-5154: Integer overflow in shared memory allocation. Credit to Google Chrome Security Team (Chris Evans).
- CVE-2012-5155: Missing Mac sandbox for worker processes. Credit to Google Chrome Security Team (Julien Tinnes).
- CVE-2012-5156: Use-after-free in PDF fields. Credit to Mateusz Jurczyk, with contribution from Gynvael Coldwind, both of Google Security Team.
- CVE-2012-5157: Out-of-bounds reads in PDF image handling. Credit to Mateusz Jurczyk and Gynvael Coldwind, both of Google Security Team.
- CVE-2013-0828: Bad cast in PDF root handling. Credit to Mateusz Jurczyk, with contribution from Gynvael Coldwind, both of Google Security Team.
- CVE-2013-0829: Corruption of database metadata leading to incorrect file access. Credit to Google Chrome Security Team (Juri Aedla).
- CVE-2013-0830: Missing NUL termination in IPC. Credit to Google Chrome Security Team (Justin Schuh).
- CVE-2013-0831: Possible path traversal from extension process. Credit to Google Chrome Security Team (Tom Sepez).
- CVE-2013-0832: Use-after-free with printing. Credit to Google Chrome Security Team (Cris Neckar).
- CVE-2013-0833: Out-of-bounds read with printing. Credit to Google Chrome Security Team (Cris Neckar).
- CVE-2013-0834: Out-of-bounds read with glyph handling. Credit to Google Chrome Security Team (Cris Neckar).
- CVE-2013-0835: Browser crash with geolocation. Credit to Arthur Gerkis.
- CVE-2013-0836: Crash in v8 garbage collection. Credit to Google Chrome Security Team (Cris Neckar).
- CVE-2013-0837: Crash in extension tab handling. Credit to Tom Nielsen.
- CVE-2013-0838: Tighten permissions on shared memory segments. Credit to Google Chrome Security Team (Chris Palmer).
Happy cross-browser testing in Chrome 24!
Email this blog post to your friends or yourself!
Try Browserling!
Enter a URL to test, choose platform, browser and version, and you'll get a live interactive browser in 5 seconds!

 Subscribe to updates!
Subscribe to updates!
 BizSpark
BizSpark